Overview
The following Demo Outline assumes you are familiar with the product and does not go into all the details you may want to communicate while demonstrating the product. If you are not familiar with Netop Connect its recommended you review the Netop Overview and Security Server training modules before reviewing this module.
What is Connect?
Netop Connect provides remote access and KVM control to nearly every platform or device using a proprietary connection protocol that rides over TCP, UDP and/or HTTPS. Deployment options can be On Premises or Public cloud SaaS or a combination of both or VPC.
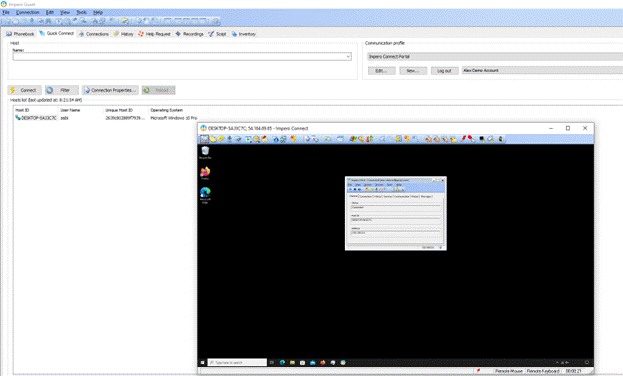
- Show the Guest module connecting to a Host module either through the Portal or direct TCP connection.
- Explain connectivity options, portal or TCP/IP.
- TCP runs on 6502 TCP or UDP, runs exclusively on customers infrastructure, LAN/WAN/VPN connections needed to support connectivity.
- Benefits:
- No network traffic traverses the public Internet.
- All authentication protocols are internal resources.
- Netop Connect is an all software solution, no third party hardware appliances.
- Portal Guest
- Show how Guest authenticates into Portal.
Explain authentication options:
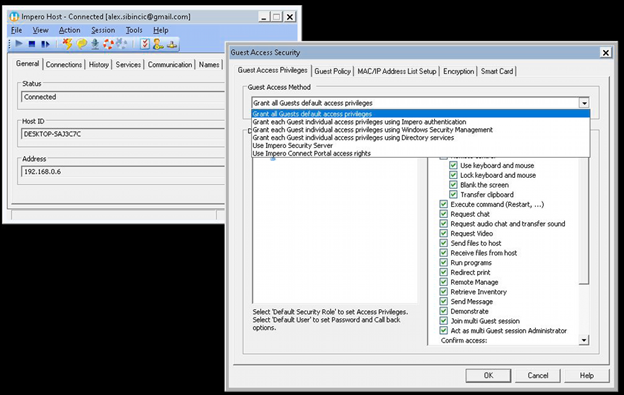
Once connected go to the Host GUI and go to the Tools>Guest Access Security section:
All Guests have the same password - all users that connect will be prompted for the same password and receive the same role assignment. Good for simple deployments that do not require more security.
Each Guest has its own password - Individual "Netop Connect" users and groups can be created and given unique security roles for more granular security. Not the best security but better than one password.
Use Windows Security Management - User will be challenged with local or domain users that are in the local groups of the Host computer and have been given permissions for remote access. AD or local users or groups are used to give granular access roles for remote sessions. Host will communicate to AD via Windows Networking to validate credentials or query local security to allow access.
Use centralized security management with the Netop Security Server - this will instruct the Host to use the Security Server to authenticate the user, details on this are in the next section.
Use Portal Access Rights - Anytime a user connects through the Portal communication profile or the browser interface the "Role Assignments" will always be processed in the Portal, so the user needs to have permissions set in the Portal Role Assignments for the user to have access to the devices they need as determined by the Portal administrator.
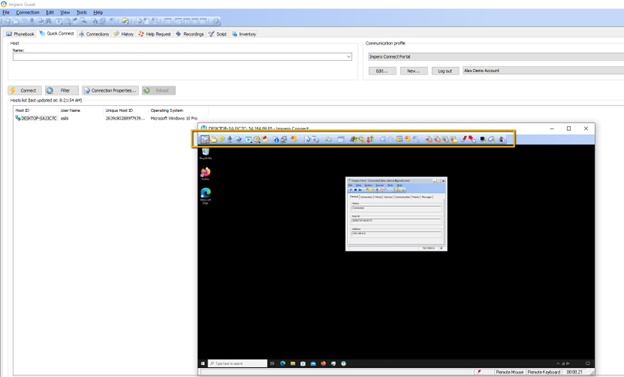
Explain each feature going across the connection toolbar
- File Transfer:
- Only available in the Guest module (browser file transfer on the roadmap).
- Guest user inherits permissions of the remote logged in user.
- Transfer speed is relative to the network speed, it will use all bandwidth available. Also HW/SW specifications will be a factor.
- Remote Management
- CMD Window - user can elevate permissions using a administrator password for the session.
- User inherits remote user logged in permissions so features are bound by permissions like ability to restart services etc...
- CMD Window - user can elevate permissions using a administrator password for the session.
- Chat
- Clipboard exchange
- Can be controlled in the Guest module and disabled via a role assignment
- Application Whitelist
- Create security roles that filters out all other visible applications except on the "whitelist"
- Blank Screen
- New version allows more flexibility allowing for custom text instead of just blanking the screen.
Review the tabs on the Guest
- Phonebook
- Predefined records of endpoints that be customized and managed by the Netop admin
- Guest can be configured to point to shared resource for common access for all Guest users making it easier to manage.
- Predefined records of endpoints that be customized and managed by the Netop admin
- Quick Connect
- Ad hoc connections to remote computers instead of Phone book files
- Ad hoc connections to remote computers instead of Phone book files
- Connections
- Simply displays active connections
- History
- A record of all connections, these are also formatted as Phonebook files so you can easily copy and paste them into the Phonebook tab for easy creation of a Phonebook file.
- A record of all connections, these are also formatted as Phonebook files so you can easily copy and paste them into the Phonebook tab for easy creation of a Phonebook file.
- Scripting
- Automate Netop features into a script.
- Elevate permissions within the script to run processes and tasks with admin permissions within the script.
- Recording
- Propriety recording format that cannot be altered, can be used as evidence in a court of law.
- Can only be played back with the Guest module.
- Inventory
- Hooks into the Windows "System Information" utility and compiles the data into an XML file that is saved in the logged in Guest Users folder.
- It is a snapshot of the inventory and can be imported into asset management tools but is not an asset management system per se.
- Hooks into the Windows "System Information" utility and compiles the data into an XML file that is saved in the logged in Guest Users folder.
Explain Host module configuration:
- Authentication
- Review authentication options if needed
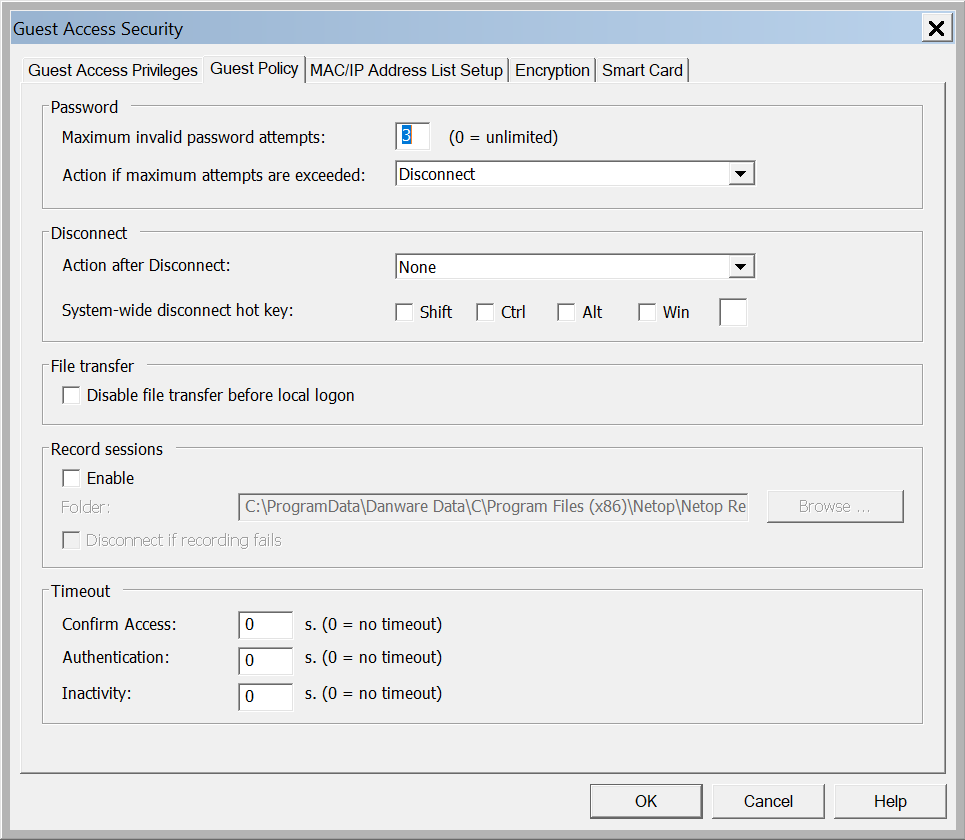
- Guest Policy
- Review location options for Host recording file
- Inactivity timeout is important for compliance
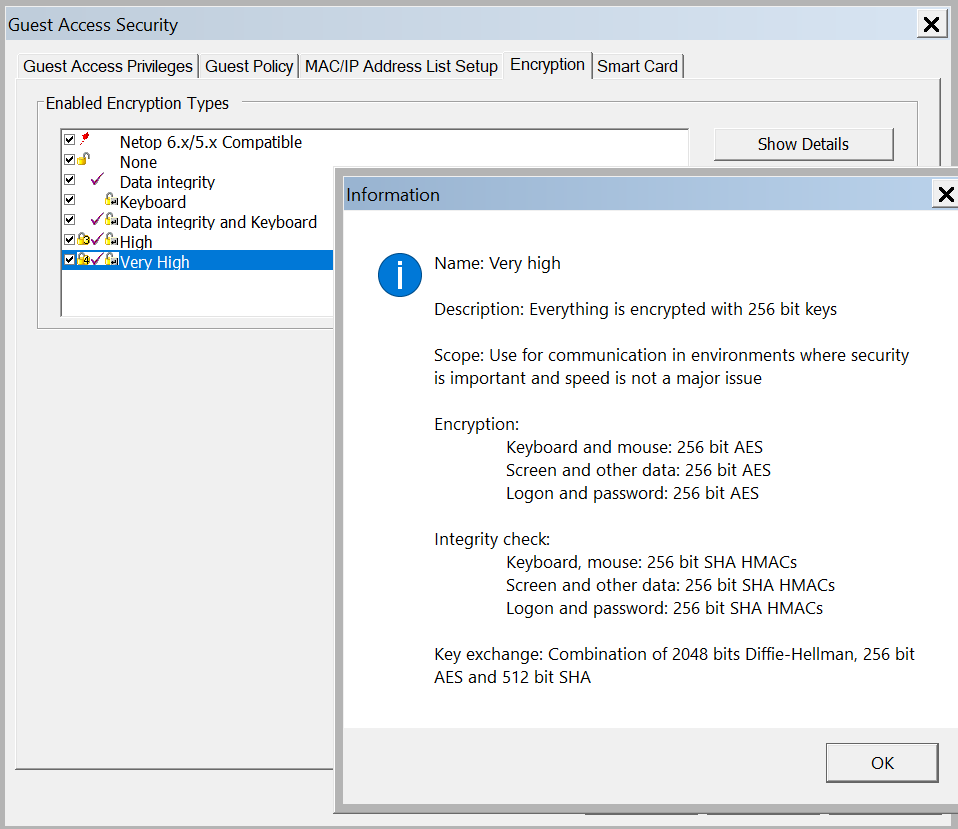
- Encryption
- Talk about the encryption levels, important for compliance
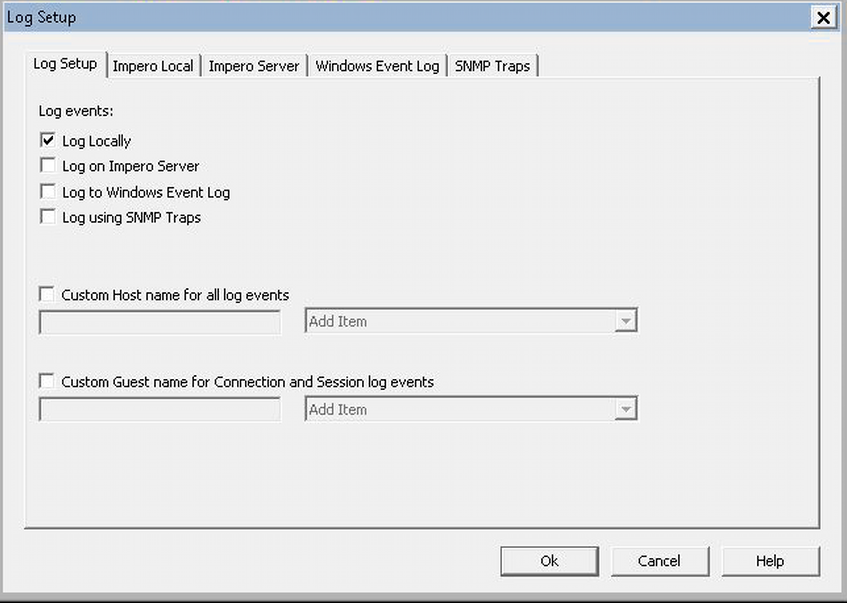
- Event logging
- Review the event logging destination options.
- Review the event logging destination options.
How to become compliant
- MFA
- Security Server is required for on premise MFA
- Portal has native MFA via email token delivery only
- Portal can use ADFS to redirect authentication
- Event Logging
- Encryption
- Authentication protocols,
- ADFS
- Kerberos via LDAP in Security Server
- MFA
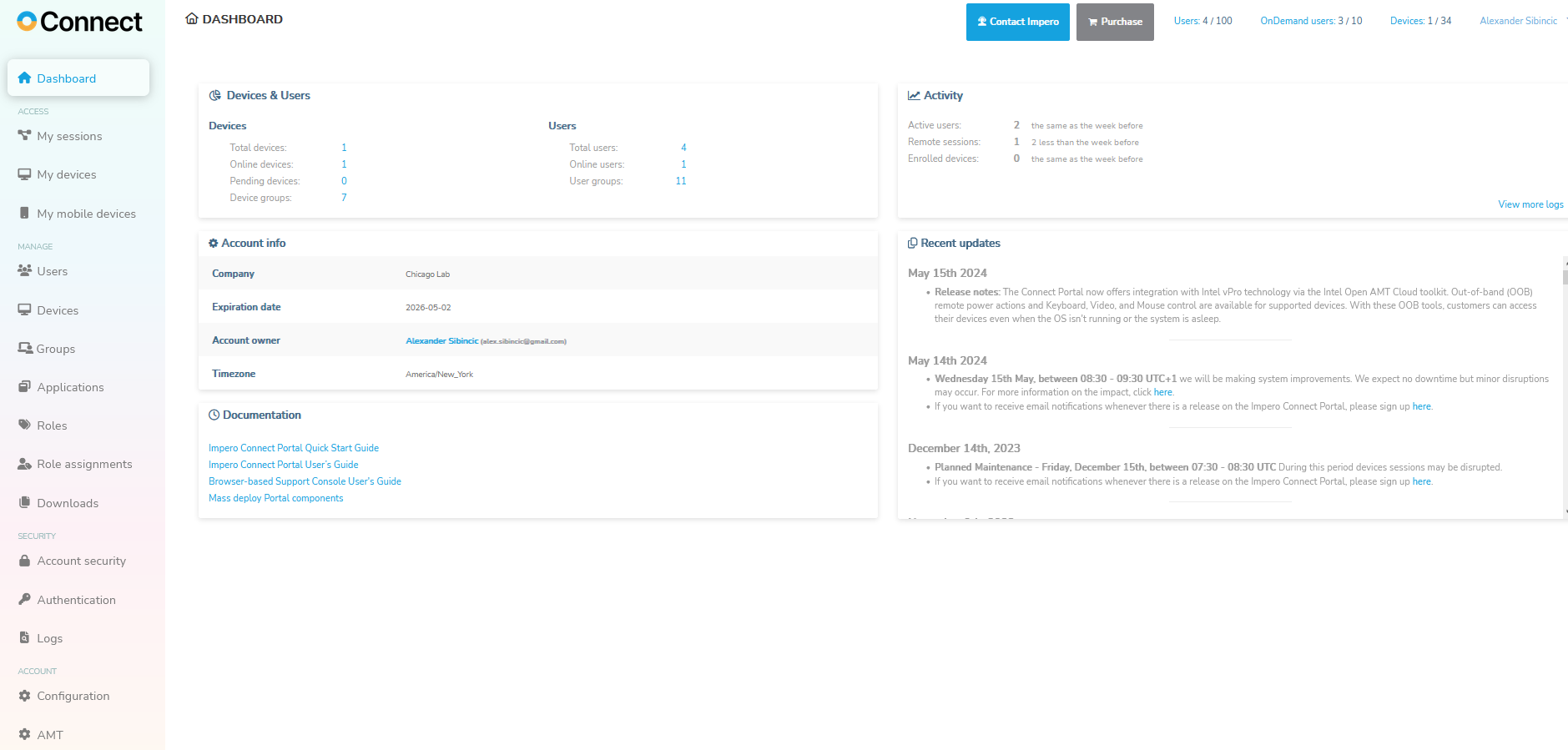
Go over the Portal Interface and features
- My Devices
- These are the devices the logged in user are allowed to control as defined by the Portal admin.
- On Demand - My Sessions
- Connect to devices that do have the Host module installed
- Connect to devices that do have the Host module installed
- Add users
- Invite users to create their own password and assign security groups and user roles for security upon user record creation.
- If Portal is using ADFS, AD groups will be imported to create role assignments and when a user within the group logs in for the first time the user record will be created then.
- User and Device groups
- Users and devices should be added to groups to create Role Assignments to allow access to only the devices determined by the Portal administrator.
- Users and devices should be added to groups to create Role Assignments to allow access to only the devices determined by the Portal administrator.
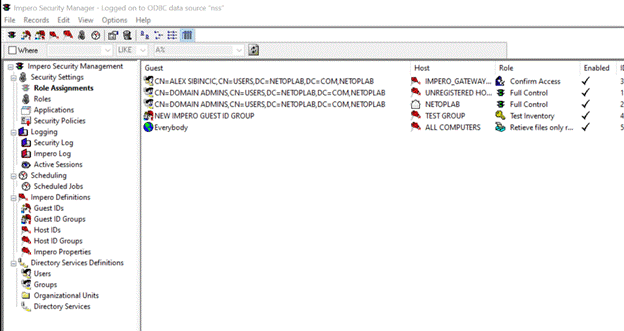
- Role Assignments
- Create security policies we call role assignments to give access to users and groups to groups of devices, once they are allowed access what are they allowed to do in terms of "roles', these roles are features you want these users to have once they allowed access.
- Open a role and show the granularity to see what can be allowed or denied.
- The most restrictive role takes precedent if a user is in 2 or more roles.
- Create security policies we call role assignments to give access to users and groups to groups of devices, once they are allowed access what are they allowed to do in terms of "roles', these roles are features you want these users to have once they allowed access.
- Activity Logs
- Event activity is collected in the Portal by default of all activity. who connected to what device and every action.
- All changes made in the Portal are also collected for compliance purposes.
- Event activity is collected in the Portal by default of all activity. who connected to what device and every action.
- ADFS/LDAP options
- The Portal has options to integrate into a customers ADFS instance either self hosted or in Azure.
- Also supported is an LDAP integration for authentication and to lookup and validate AD users and groups.
Security Server Overview
- Role Assignments
- AD groups can be mapped to groups of devices to allow or deny access and then what Netop feature are they allowed to use while accessing the device.
- Same logic as the Portal role assignment.
- LDAP (Directory Services)
- Security Server integrates to AD using LDAP, create a binding to an AD to leverage AD groups and users for centralized user administration.
- Windows networking lookup
- Security Server can also lookup an AD using "Windows Networking" protocol to find a Domain, this is a legacy protocol and LDAP is preferred.
- Security Server can also lookup an AD using "Windows Networking" protocol to find a Domain, this is a legacy protocol and LDAP is preferred.
- Netop Connect Users
- Netop users and groups can also be created if you don't want to connect to the AD
- Netop users and groups can also be created if you don't want to connect to the AD
- Event Log
- All log events can be collected into the SQL datbase for centralized collection point for easier reporting.
- Can also be exported as a "Syslog" format for ingestion into other repositories.
- SQL
- Supports various SQL engines so customers can use already existing technology.
Was this article helpful?
That’s Great!
Thank you for your feedback
Sorry! We couldn't be helpful
Thank you for your feedback
Feedback sent
We appreciate your effort and will try to fix the article